Theory of Programming and Artificial Intelligence

We conduct a wide range of research on basic theory and applications of computational intelligence, mathematical informatics, and software engineering. Specifically, we promote research on machine learning algorithms, mathematical programming, distributed algorithms, software measurement and analytics, mining software repositories, human behavior analysis, human-machine interaction, computer vision and so on.
 |
|
|---|
Development of distributed algorithms for multiagent systems
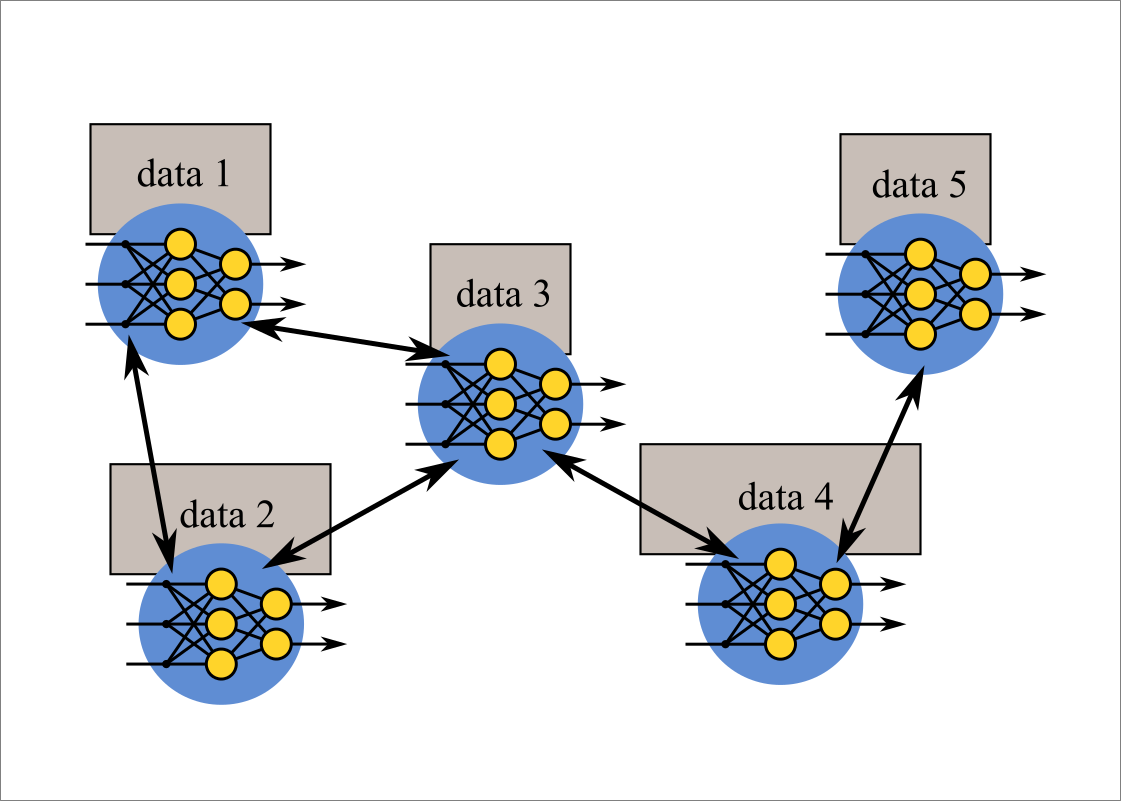
I am studying methods for multiple agents to solve problems in a distributed and cooperative manner. Specifically, I design distributed algorithms for agents to solve given large-scale problems efficiently under the situation that each agent can communicate only with a small number of neighboring agents, and apply them to principal component analysis, nonnegative matrix factorization, and federated learning.
 |
|
|---|
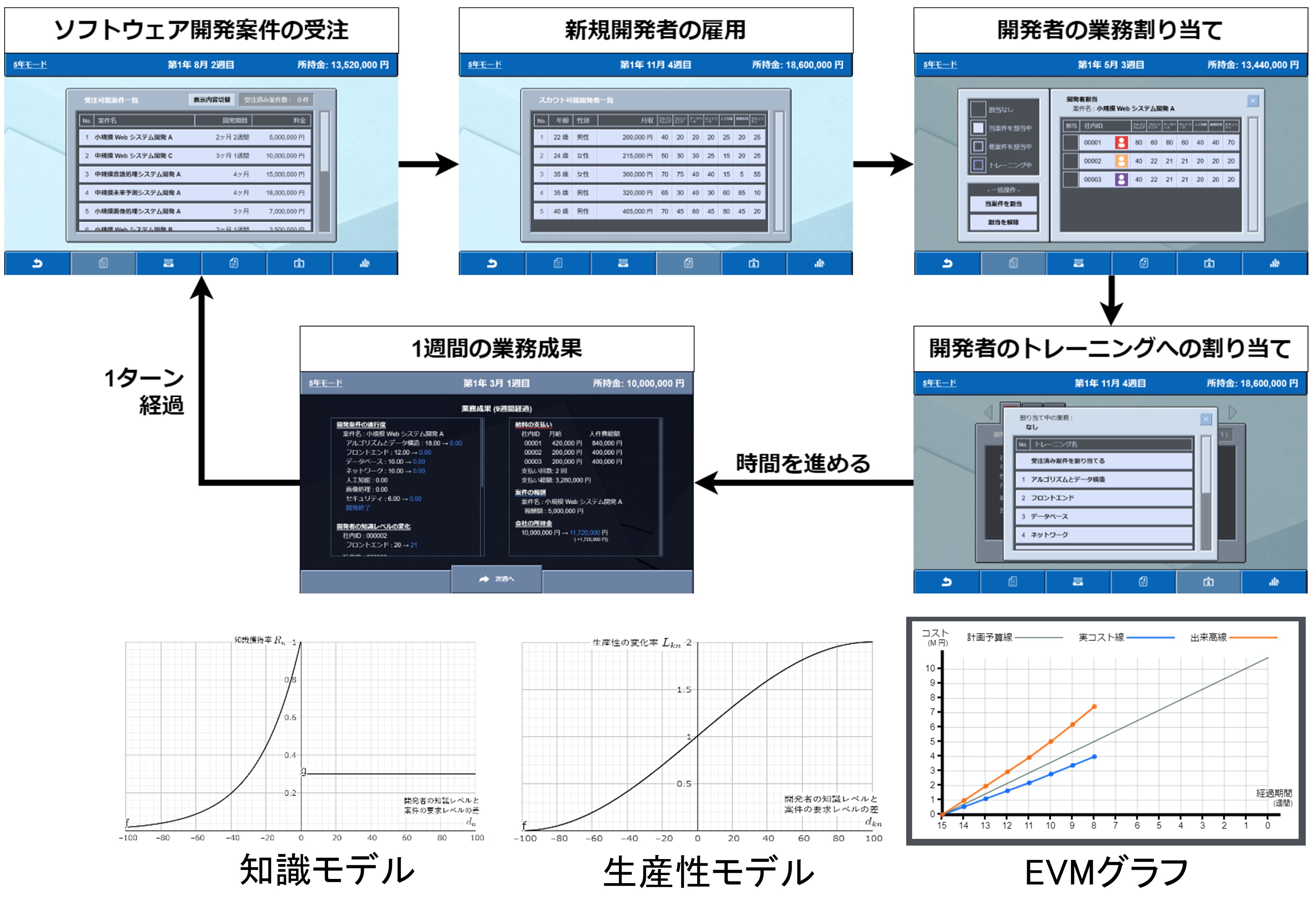
Development of software project management simulator
In this study, we are developing a simulator for learning quantitative software development management (https://www.okayama-u.ac.jp/user/salab/spm/). The simulator enables us to learn effort estimation, developer assignment considering their skills, schedule and cost management considering productivity factors, and engineer skill development through on-the-job training.
 |
|
|---|
We aim to realize self-adaptive systems and multi-agent systems that autonomously monitor and analyze the current situation, consider the next strategy to take, and change their own behavior to achieve their goals. We are also studying next-generation technologies for designing and implementing autonomous software, such as technologies for automating software development and automatically discovering user requirements.
 |
|
|---|
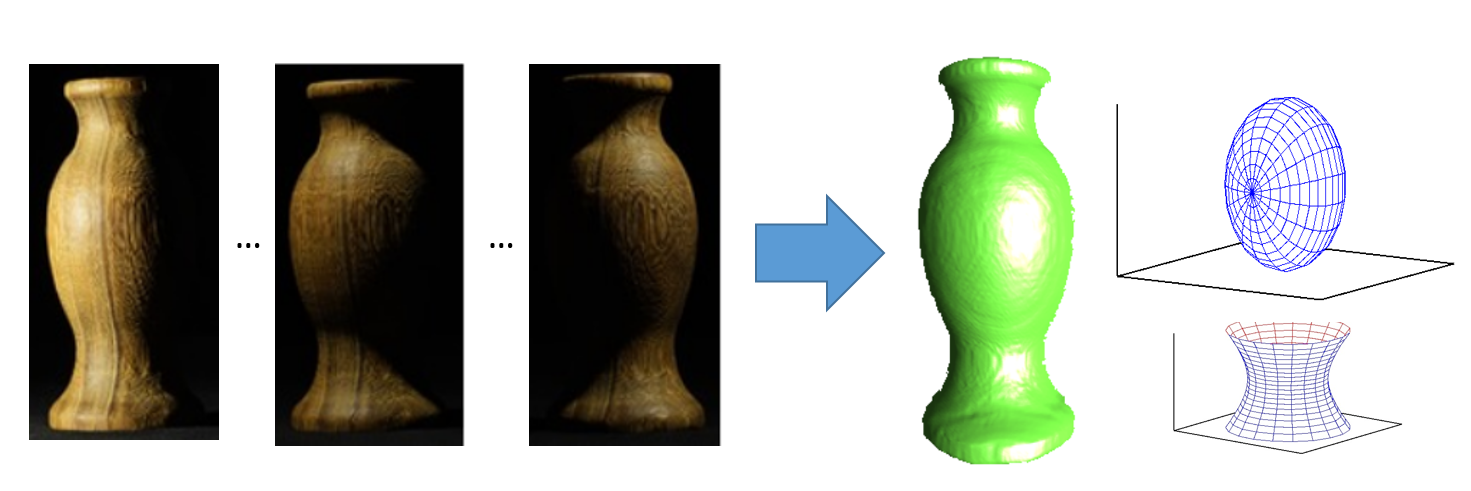
Image understanding via inverse rendering
Computer graphics algorithms generate 2D images from 3D parameters, such as shape and pose of each object in a 3D scene, considering laws of optics and geometry. Its inverse problems analyze 2D images to reconstruct 3D parameters, which enables computers to understand or accurately measure objects in a 2D image. I am studying efficient numerical optimization methods required for such inverse problems.
.jpg) |
|
|---|
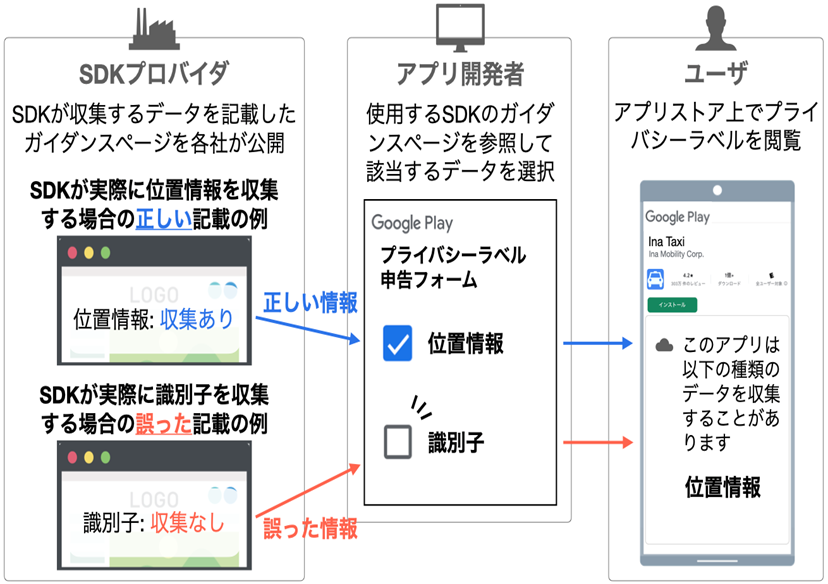
Our goal is to understand and solve challenges in computer security and privacy leakage. We collect and analyze released software without source code. In recent years, we have focused on Android applications. We study various analysis techniques, such as static and dynamic taint analyses, native code analysis, and network traffic analysis. We aim to improve these analysis techniques and also utilize them to investigate privacy leakage in real-world Android applications.
 |
|
|---|
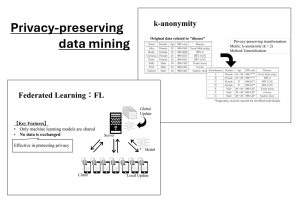
We conduct research on privacy-preserving data mining, a technology that enables the secure utilization of data containing personal information. Our current focus is on federated learning, in which multiple data holders collaboratively build AI models while preserving privacy. We aim to develop novel techniques that achieve a balance between privacy protection and utility.

_NAKAGAWA.png)